Bluetooth is a wireless technology designed for close-range connections. You use it every day with headphones, speakers, and other devices. But, with that convenience comes a question: can other people connect to your Bluetooth devices without your permission?
It’s unlikely someone can connect to your Bluetooth without you knowing, but it’s not impossible. Here’s why:

Modern Bluetooth Security:
- Pairing: Most Bluetooth devices now require a pairing process. This involves both devices agreeing to connect and often confirming a code or prompt. This makes it difficult for someone to connect without your explicit permission.
- Encryption: Bluetooth connections use encryption to scramble data being transmitted. This makes it much harder for someone to intercept and understand your information even if they manage to connect.
- Limited Range: Bluetooth has a limited range, usually around 30 feet. Someone would need to be relatively close to your device to attempt a connection.
However, there are some things to keep in mind:
- Older Devices: Older Bluetooth devices with outdated versions of the technology might have weaker security.
- Bluetooth Attacks: While less common these days, there are still Bluetooth attacks like “bluesnarfing” (stealing data) and “bluejacking” (sending unsolicited messages) that could be attempted.
- Leaving Bluetooth Discoverable: If you leave your Bluetooth discoverable, it makes it easier for others to see and attempt to connect to your device.
To protect yourself:
- Turn off Bluetooth when not in use: This is the simplest way to prevent unwanted connections.
- Pair only with trusted devices: Be cautious about pairing with unknown devices.
- Keep your device’s software updated: Updates often include security patches that address vulnerabilities.
- Disable discoverability: Make your device undiscoverable in Bluetooth settings when you’re not actively pairing with a new device.
- Be aware of your surroundings: Be mindful of who is around you, especially in public places, as someone could attempt to connect if they are close enough.
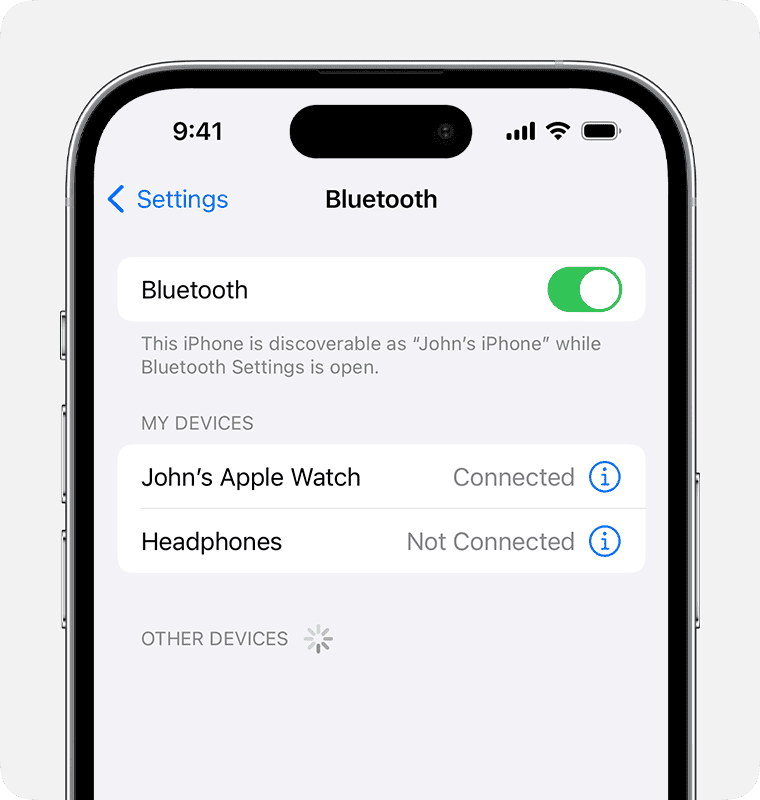
In most cases, you’ll be notified if someone tries to connect to your Bluetooth. You’ll usually see a pairing request or notification on your device’s screen. Don’t accept any pairing requests from unknown devices.
If you’re concerned about someone accessing your Bluetooth without your knowledge, consider using a strong password or PIN on your device and enabling two-factor authentication for added security.
Understanding Bluetooth Security
The short answer is yes, but it’s not quite that simple. Here’s what you need to know:
Bluetooth Pairing
To connect to a Bluetooth device, a user’s device must pair with yours. Here’s how the process works:
- Discovery Mode: Your Bluetooth device needs to be in “discovery mode” to be visible.
- Scanning: The other person’s device scans for available Bluetooth devices within range.
- Pairing Request: They’ll see your device on their list and can send a pairing request.
- Confirmation: You’ll need to confirm the pairing request on your device. Often, this includes a passcode.
Bluetooth Security Risks
Here’s where potential security issues come in:
- Always On Discovery Mode: If you accidentally leave your device discoverable, anyone within range can see it and try to pair.
- Weak Passcodes: Using easily guessable passcodes (like 0000 or 1234) makes your connection vulnerable.
- Bluetooth Vulnerabilities: Rarely, flaws might exist in Bluetooth itself. Staying updated with the latest software patches is important.
How To Protect Yourself
Protecting yourself from unwanted Bluetooth connections is simple:
| Tip | Description |
|---|---|
| Turn Off Discovery Mode | When you’re not actively using Bluetooth, turn off discovery mode so your device isn’t visible to strangers. |
| Use Strong Passcodes | If your device requires a passcode for pairing, always pick something complex and hard to guess. |
| Stay Updated | Install the latest operating system and security updates for your devices. |
| Be Careful in Public | Be aware of your surroundings in crowded areas and be cautious about accepting pairing requests. |

Remember:
It’s very unlikely that someone can connect to your Bluetooth without your knowledge. Just follow the simple steps above to stay safe!
Understanding Bluetooth Connectivity
This section zeroes in on how Bluetooth technology allows devices to connect, covering the essential concepts, the process of pairing, and the effective range and power of Bluetooth connections.
Basics of Bluetooth Technology
Bluetooth is a wireless communication technology that enables devices to exchange data over short distances. It’s commonly embedded in a wide variety of devices, from smartphones to headphones. Using radio waves in the 2.4 to 2.485 GHz band, Bluetooth allows devices to establish a connection without the need for cables.
Pairing Bluetooth Devices
For two Bluetooth devices to connect and communicate, they must first be paired. This involves making one device discoverable, where it sends out a signal that others can find, while the second device searches for this signal. Once they locate each other, a connection is typically secured with a PIN code to ensure that only authorized devices can pair.
- Turn on Bluetooth on both devices.
- Ensure one device is set to “discoverable” mode.
- Select the discoverable device from the other’s Bluetooth search list.
- Enter a PIN code if prompted.
The Range and Strength of Bluetooth Connections
Bluetooth connections have a limited range, typically up to 10 meters (33 feet) for most devices, but some may reach further. The strength and quality of a Bluetooth signal can be influenced by obstacles like walls or interference from other electronic devices. While standard connections may suffice for devices nearby, specialized technology like Bluetooth 5.0 offers a significantly improved range and stronger connection.
- Standard Bluetooth range: Up to 10 meters.
- Obstacle impact: Walls and electronic interference can weaken the signal.
- Advanced Bluetooth technology: Bluetooth 5.0 extends range and improves connectivity.
Protecting Your Bluetooth Devices from Unauthorized Access
It’s vital to stay vigilant and know how to shield your Bluetooth devices from unwelcome intrusions. By understanding the risks and implementing security measures, you can enjoy the convenience of Bluetooth without compromising safety.
Common Bluetooth Security Risks
Bluetooth technology, while convenient, can open the door to security breaches if not properly managed. Unauthorized access to devices can lead to personal data theft or the unintended sharing of sensitive information. A common concern is bluebugging, where hackers exploit Bluetooth connections to take control of a device without the owner’s knowledge. Other risks include eavesdropping, where attackers intercept the data being transmitted between devices, and bluejacking, which involves sending unsolicited messages to Bluetooth-enabled devices.
Securing Your Bluetooth Connections
To enhance Bluetooth security, always use a strong, unique PIN when pairing devices, as this can prevent unauthorized access. Make sure your device uses the latest version of Bluetooth with enhanced data encryption to safeguard your privacy. Disable Bluetooth when it’s not in use to minimize risks, and avoid automatic pairing, as this can leave you vulnerable to cyberattacks. Change default passwords immediately to something more secure and complex. Enable “non-discoverable” mode when Bluetooth is not actively being used.
- Turn off Bluetooth: When not needed, keep Bluetooth disabled.
- Update regularly: Ensure your device’s software and Bluetooth firmware are up-to-date.
- Manage paired devices: Regularly review your list of connected devices and remove any that are unfamiliar or no longer in use.
Preventing and Responding to Bluetooth Attacks
Stay aware of signs that may indicate a Bluetooth attack, such as unexpected requests for pairing or sudden drops in device performance. Should you suspect a compromised Bluetooth connection, immediately disconnect the devices and disable Bluetooth. Afterward, monitor your device for any unusual activity and consider changing your security credentials. In some situations, using a VPN can help secure your data transmission over Bluetooth. It’s also worthwhile to frequently check for security updates that address newly discovered vulnerabilities.
- Stay informed: Be aware of the latest Bluetooth attacks and how to prevent them.
- Control visibility: Use settings to make your device non-discoverable to others.
- Be cautious with pairing requests: Only accept connections from trusted devices.
Mitigating Risks Associated with Bluetooth Technology
Bluetooth technology connects devices seamlessly, but it also creates avenues for unwanted access. Protecting sensitive data and devices requires understanding the threats and practicing secure Bluetooth use.
Understanding Vulnerabilities of Bluetooth Pairing
Bluetooth hacking often begins with the pairing process. When devices pair, they exchange security keys, making this a critical phase for eavesdroppers. There are numerous hacking techniques, such as bluejacking, which involves sending unsolicited messages, and bluesnarfing, which is the unauthorized access of information from a wireless device through a Bluetooth connection. To combat these, ensure that all devices are set to ‘non-discoverable’ when not actively pairing, and only pair with known devices in private settings.
Techniques to Avoid Eavesdropping and Data Theft
Preventing unauthorized access is vital, especially since hackers can track activities or contact information from devices like smartphones, Bluetooth headphones, and speakers. Encryption is a strong line of defense. It scrambles data so only intended recipients can decipher it. Always use devices that support the latest encryption standards. Additionally, when not in use, turn off the Bluetooth function, particularly in public areas where the risk of intrusion is higher.
- Keep devices updated: Regular updates often contain security improvements.
- Manage paired devices: Review and remove unfamiliar or unnecessary connections regularly.
- Use security software: It can help detect and block suspicious activity.
Implementing Best Practices for Bluetooth Use
Beyond encryption and cautious pairing, there are best practices that can enhance security. For example, regularly changing pins and passwords deters bluebugging, where hackers take control of a phone to make calls or send texts.
- Parental supervision: If children use Bluetooth devices, parents should monitor their pairing activities and educate them about security.
- Limit sensitive transactions: Avoid using Bluetooth for transactions that reveal sensitive details or contact information.
- Regular scanning: Implement routine security scans for any suspicious Bluetooth activity.
By staying vigilant against security threats and adhering to these practices, users can enjoy the convenience of Bluetooth technology with minimized risk.
Frequently Asked Questions
Bluetooth technology has made connecting devices wirelessly a breeze, but it also raises questions about security and privacy. Here are some clear answers to common inquiries about Bluetooth connectivity.
How can I determine if an unknown device is connected to my Bluetooth?
Check your device’s Bluetooth settings where paired and connected devices are listed. If you see a device you don’t recognize, it might be connected to your Bluetooth.
What steps should I take if I suspect my Bluetooth device has been compromised?
Change your device’s security settings immediately, including the PIN or password. Perform a software update, as this can fix known vulnerabilities. If you still have concerns, consider factory resetting the device.
How can I prevent unauthorized access to my Bluetooth devices?
Always use a strong, unique PIN for pairing, and turn off the discoverability of your devices when not in use. Make sure to keep your device’s software up to date.
Is it possible for someone to hijack my Bluetooth headphones while I’m using them?
Technically, it’s possible, but such an occurrence is uncommon. Nevertheless, keep the firmware updated and maintain a non-discoverable status when in crowded areas to reduce the risk.
What are the risks of leaving my Bluetooth visible to all nearby devices?
Leaving Bluetooth visible can expose your device to unwanted pairing requests and potentially to security threats, such as data interception or unauthorized access.
What security measures are in place to protect Bluetooth connections from unwanted access?
Bluetooth employs several security measures including authentication, encryption, frequency hopping, and service levels which aim to secure the connections against unauthorized access.